This will ban IPS that fail to login after so many times.
Make a firewall inbound Rule called BlockAttackers that is a blacklist (block all ports. scope Remote IP address: these IP address)
Make a powershell script
$DT = [DateTime]::Now.AddDays(-1)
$l = Get-EventLog -LogName 'Security' -InstanceId 4625 -After $DT | Select-Object @{n='IpAddress';e={$_.ReplacementStrings[-2]} }
$g = $l | group-object -property IpAddress | where {$_.Count -gt 20} | Select -property Name
$fw = New-Object -ComObject hnetcfg.fwpolicy2 # get firewall object
$ar = $fw.rules | where {$_.name -eq 'BlockAttackers'}
$w = $g | where {$_.Name.Length -gt 1 -and !$ar.Name.contains($_)}
or download this one ps-get-ipaddr-failaudit.ps1
Create task in scheduler and set trigger to event 4625 (windows login including terminal services). But you can set trigger to run e.g. twice per hour to avoid unnecessary loading the server.
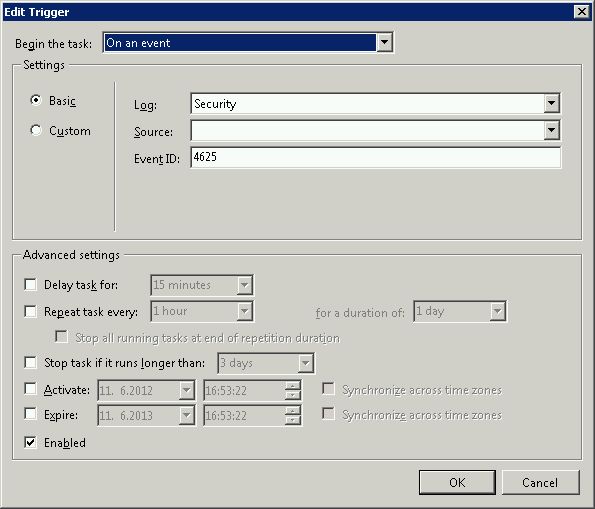
and after trigger run powershell script. You must also set higher privileges to run this script, otherwise it will fail with security exception.
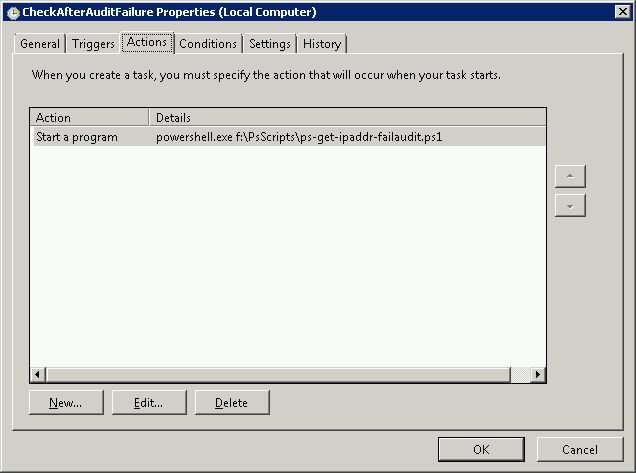
You can also bind this script to other security events.